Spying is fashionable. Lately, Germans realized this when information about Angela Merkel‘s spying by the Nation Security Agency (NSA) came to light. Our western neighbors have taken actions to encrypt messages and information with typewriters. Returning to Enigma times? We do not know that. But take a look at the short history of encrypting machines.
Skytale

Skytale is one of the first known encrypting tools. It takes its origin from ancient Greece where it was used, among others, by Spartans. How did it worked? A parchment with a message was rolled up on the piece of carved wood. To decipher it, another piece of wood, of the same diameter, was needed, so the letters could form a string of words.
Jefferson‘s disc

This tool was created about year 1790, but it was so advanced that American soldiers used it even 150 years later, during the Second World War (it was called M-94 then). This device consisted of 36 discs. On each of them, the alphabet was written, in random order. Thanks to such a large amount of discs the code was practically unbreakable and the number of possible combinations was huge.
M-209

The machine was designed by the United States Navy. It was used mainly during the Second World War, but also during the Korean War (1950-1953). Encrypting was performed by setting the 6 discs in random order and by using special knobs. The message was printed on a tape. To read it, the receiver needed to know the same pattern of discs.
Enigma

The most famous machine of the Second World War was used commercially, but it became famous thanks to Third Reich German army. Every encrypted message had its own settings, based on a printed book of codes. It appeared that the Enigma code was unbreakable but Polish and British cryptologists managed to crack it. At the end of the war every message was decoded and decoding took 1 day generally.
Lorenz‘s encrypting machine
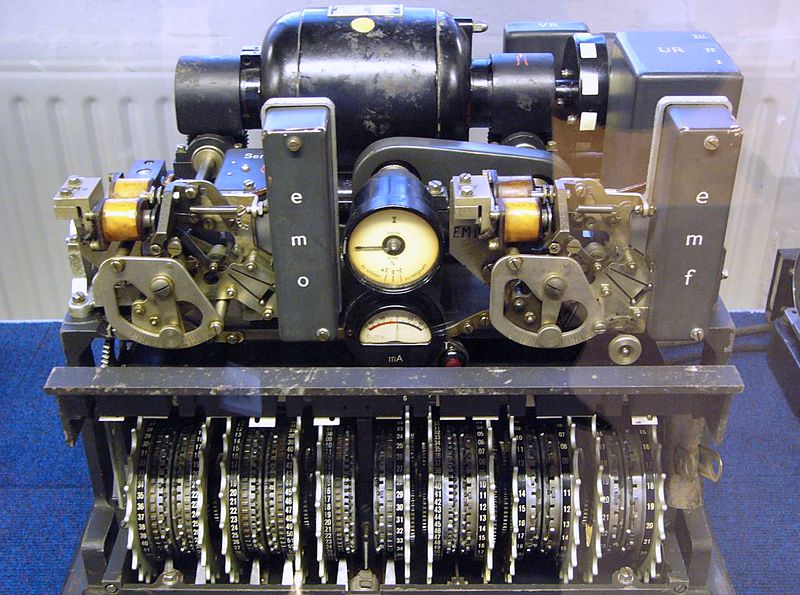
This device was called a ‘tuna fish‘ by the British. It resembled Enigma but it worked basing on different principles. It was also used during the Second World War, but because of its weight and the fact that it could not be used in the field, it was used to send messages of higher priority and importance. Encrypting was possible thanks to 12 cryptographic wheels, 5 of which turned irregularly, 5 of them regularly, two other controlled the work of the rest. The message was generated as Baudot code.
Enigma 2

Now let‘s take a look at modern devices. Enigma, which was quite large and heavy, was transformed into a small mobile phone. What this device is capable of? Every connection is put through two stages of encryption – authentication and encoding. During these processes the sound is protected by a special 256-bits algorithm. It is also a moment of creating a special key which is, according to many experts, very hard to crack. Cracking it might took even couple of years. To establish such an encrypted call, the telephone must be used by both participants of the conversation.
Electronic data encryption

In previous years, special machines were used to send encrypted information. But since the electronic and computer era has emerged, protection of data is digital – it is performed in form of bit keys. It is recommended especially for businessmen who need to protect their valuable and confidential information.










Leave a Reply