You use it every day: when you open your car door with the remote control, unlock access to a building by putting your entry card to the reader or pay with a contactless card. Although these are just a substitute for RFID applications, it is easy to conclude that RFID has revolutionised wireless communication. What exactly is it, how does it work and what dangers does it pose? We explain!
RFID technology – what is it?
RFID stands for Radio Frequency Identification. It is a form of wireless communication between objects and people. It collects, stores and transmits data between RFID tags and readers.
How does RFID technology work?
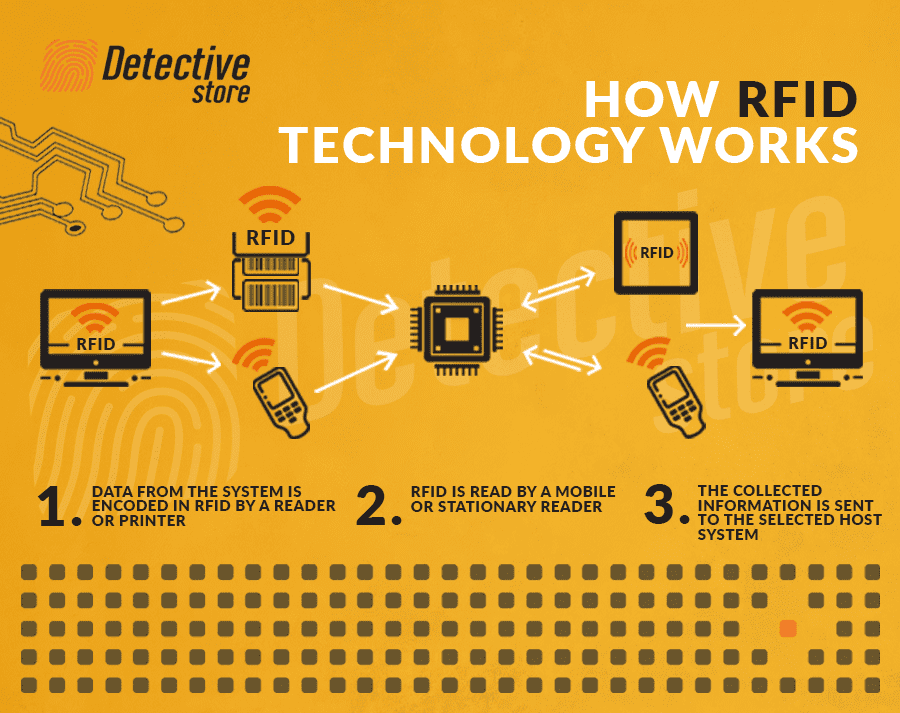
An RFID tag is a small passive or active electronic circuit. It contains a unique identifier. To read it, you use an RFID reader, a device with an antenna for radio communication, which sends radio signals towards the tag and thus activates it to respond. The identifier goes to the system and, depending on the application of the technology, it takes the appropriate action, e.g. activates the security system.
What are the RFID standards?
Due to a wide range of technical variations, such as the type of encoding or transmission speed, different RFID technology standards are distinguished. In this way, their authors ensure compatibility and interoperability between different systems.
- Tiris - one of the earliest standards; based on FM transmission and used in commercial applications,
- Unique - the simplest, yet one of the most popular standards; uses passive tags for identification, written with an identification code during production; used in access control and time tracking systems;
- Hitag - industry standard, enables data encoding; used for animal tagging and tolling systems,
- Mifare - a standard developed by Philips that combines simple memory tags with encryption-enabled processors; used in bank cards and tickets;
- EPC C1G2 - a global standard distinguished by its long read range; used in sports timing systems.
Each example of RFID standards addresses a specific need, finding applications from access control to supply chain management.
RFID technology versus barcodes
RFID technology is sometimes confused with traditional barcodes. Although both are used to mark and identify an object, it is important to remember that they are two different solutions. They are not mutually exclusive and can even be alternatives to each other.
- identification method: RFID tags have unique identifiers that can be read by readers, whereas barcodes are based on binary data (simple black and white lines and the spaces between them);
- range: RFID tags can be read from greater distances, whereas reading a barcode requires a scanline view;
- amount of data storage: RFIDs have greater capacity and in some cases offer the ability to store and update data, whereas barcodes hold a limited amount of information;
- implementation costs: RFIDs tend to be more costly to implement, unlike barcodes.
RFID security – threats to your privacy
When comparing RFID with barcodes, there is another very important aspect to bear in mind – security. RFID has become an integral part of our everyday life. Companies and individual users alike should be aware of potential threats at all times, especially to consumer privacy. Like other technologies, the solution is vulnerable to cyber attacks. The risks of unauthorized reading, interception of transaction data or theft of sensitive data, among others, should be considered in the context of the security of its use.
Beware! RFID data can be intercepted from a considerable distance! A well-known example would be the high-profile thefts on buses, where hackers hid a scanner in a bag and walked past passengers, cleaning their payment cards.
So how can the average Smith protect himself? The basic tool will be a simple gadget – the anti-RFID case. The material from which it is made (usually carbon fibre, aluminium and leather) prevents the reader from communicating with the label, thus protecting the payment card or keyless keys from data theft.
 People have bought in the last 48h!
People have bought in the last 48h!

- RFID protection
- Case for payment card, phone and keys
Another way to protect against attacks on contactless credit cards is to choose passive tags instead of active ones. Their signal is weaker: they need to be close to the reader to work, so they are harder to hack.
RFID technology in everyday life – summary
RFID technology is becoming more and more widely used in everyday life. By using it consciously and employing simple protective measures, such as anti-RFID cases, users can minimise the risk of unauthorised access or data theft. In an era of widespread digitalisation, a skilful balance between innovation and security becomes crucial to maintaining privacy and protecting data during RFID.
 People have bought in the last 48h!
People have bought in the last 48h!

- Protection against water and dust
- Personal data protection














Leave a Reply